
September 25 2023
7 min read
Jul
In project management, risks are inherent in the process. Project managers constantly strive to identify, assess, and mitigate risks to ensure the successful completion of their projects.
Two types of risks that often come into play are residual risk and secondary risk. Understanding the key distinction between these two concepts is crucial.
In this blog, we will explore the intricacies of and the differences between residual risks and secondary risks. We will also try to understand how each type impacts a project and how to manage them.
Let’s get started!
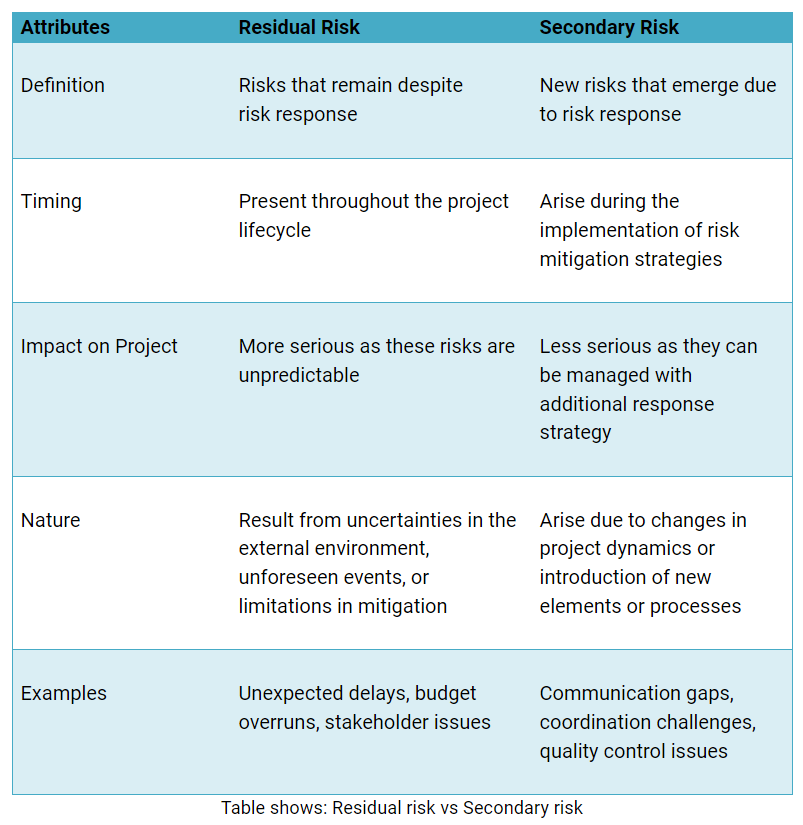
Residual risk refers to the risks that remain after risk mitigation measures have been implemented.
For example, let’s consider a construction project to build a high-rise building. During the initial risk assessment, the project team identifies the risk of unexpected delays due to adverse weather as a primary risk. They develop a contingency plan with flexible scheduling and weather monitoring tools to mitigate this risk.
In this example, the residual risk would be the possibility of delays even after implementing the contingency plan. Factors such as unusually severe weather or unforeseen complications during construction could still lead to project delays.
A secondary risk represents the new vulnerabilities that emerge from implementing risk mitigation strategies.
Let’s understand it with the same construction project scenario.
Suppose the project team now decides to hire additional contractors to speed up the construction process. In this situation, some examples of secondary risk could be the potential for communication gaps, coordination challenges, or quality control issues arising from working with new team members.
Project managers must recognize that residual risks and secondary risks require distinct approaches for effective management.
To perform effective risk management, project managers need both theoretical knowledge, historical data, and practical experience of controlling project risks. It is an ongoing learning process.
Key Takeaways
Residual risk vs secondary risk: The essential difference between the two
Residual risks are the ones that remain despite proactive risk mitigation measures, whereas Secondary risks are the ones that originate as a result of the undertaken steps to remove the primary project risks.
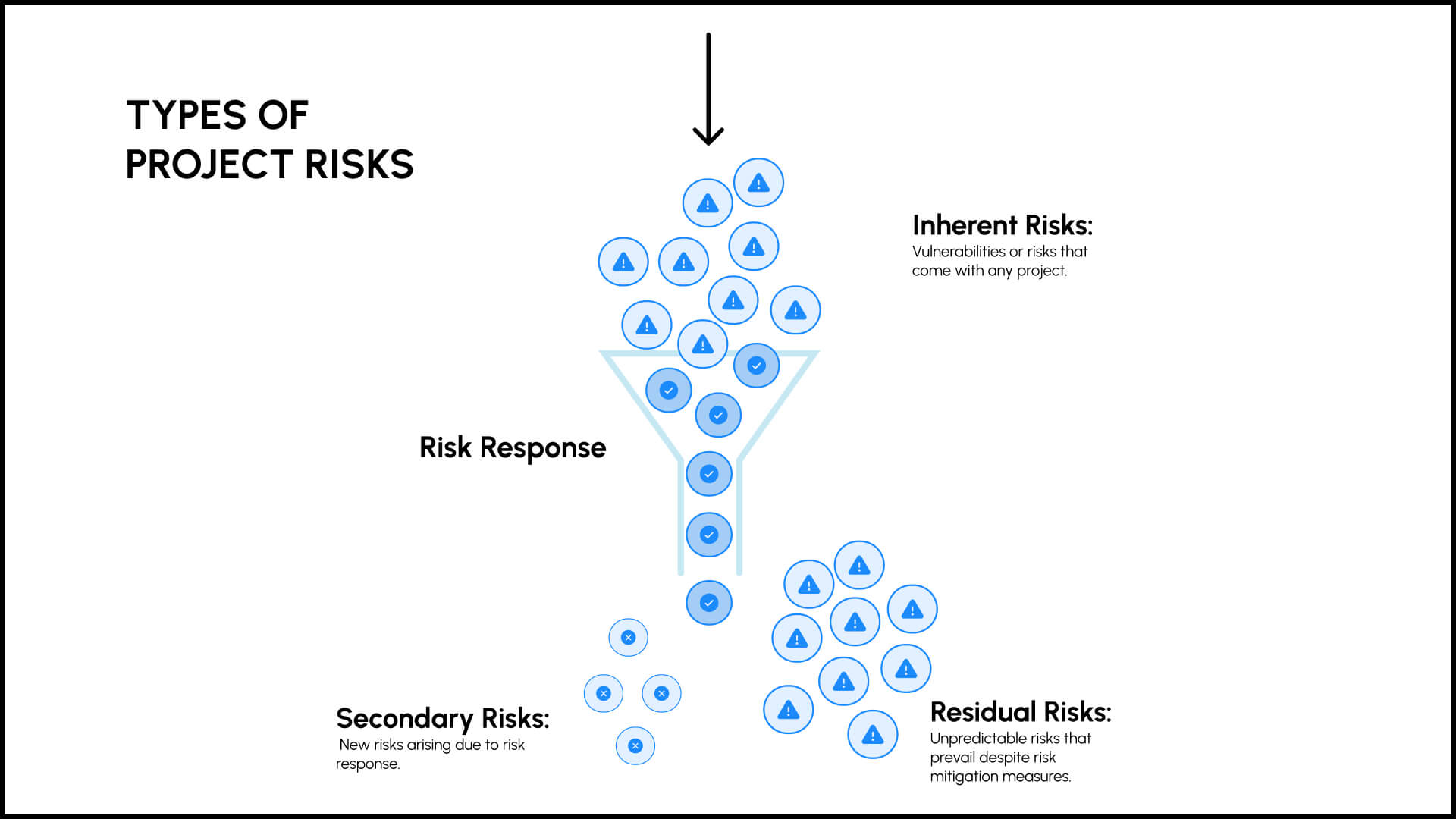
Despite proactive efforts to mitigate residual risks, they can arise due to uncertainties in the external environment, unforeseen events, or limitations in the effectiveness of risk mitigation strategies.
Residual risks may persist throughout the project lifecycle.
The impact of residual risks can range from causing minor disruptions to significant setbacks, potentially leading to project delays, cost overruns, compromised quality, or failure to achieve project objectives.
In contrast, secondary risks are the new risks that often emerge due to changes in project dynamics, the introduction of new elements or processes, or the interactions between various project components.
Secondary risks often require additional risk management actions to address them effectively.
Typically, residual risks tend to be more challenging to manage as they may be difficult to identify. Secondary risks, although introduced by risk response actions, can be anticipated to some extent and managed proactively.
Key Takeaways
Residual risk vs secondary risk: How do they impact differently?
Residual risks are typically unpredictable and therefore pose a greater challenge than secondary risks, which can be anticipated and mitigated through effective planning & strategy.
Project managers can follow the steps below to identify secondary and residual risks effectively:
Conduct a comprehensive risk assessment: Begin by conducting a thorough risk assessment of the project. Identify and document all primary risks, including the known risks associated with the project’s objectives, scope, stakeholders, and constraints. This assessment will serve as the foundation for identifying secondary risks.
Analyze primary risks: Analyze each primary risk identified in the assessment to understand its potential impacts, causes, and likelihood of occurrence. This analysis will help project managers gain insights into the interconnectedness of risks and uncover potential secondary risks.
Utilize risk categorization: Categorize primary risks based on their nature, such as technical, environmental, organizational, or external risks. By categorizing risks, project managers can identify commonalities among them and anticipate secondary risks that may arise due to similar factors.
Engage stakeholders: Involve project stakeholders, including team members, subject matter experts, and external partners, in risk identification. Their diverse perspectives and expertise can contribute to identifying secondary risks that may have been overlooked. Encourage open communication and collaboration to ensure comprehensive risk identification.
Conduct risk workshops or brainstorming sessions: Organize brainstorming sessions to identify secondary risks. Encourage participants to think beyond the primary risks and explore potential cascading effects, dependencies, or interactions between risks. Use SWOT analysis, cause-and-effect diagrams, or scenario analysisto stimulate discussions.
Review historical data and lessons learned: Reviewing historical data from previous projects or similar initiatives can provide insights into potential risks. Look for patterns and recurring issues that have impacted project success. These can include risks related to technology, resources, stakeholders, scope changes, or external factors. Project managers can also establish a feedback loop between current and future projects and update the organization’s knowledge repository for future reference.
Continuously monitor and reassess risks: Secondary risks can emerge throughout the project lifecycle, so it is crucial to establish a robust risk monitoring process. Regularly review and reassess identified risks to identify any new secondary risks that may have arisen due to changes in project circumstances or external factors.
Document and prioritize secondary risks: Once identified, document the secondary risks and their potential impacts, causes, and mitigation strategies. Prioritize these risks based on their severity, likelihood of occurrence, and possible consequences to determine which ones require immediate attention and proactive mitigation.
Integrate secondary risk management into the project plan: Ensure that secondary risk management is integrated into the overall project plan. Assign responsibility for monitoring, addressing, and mitigating secondary risks to appropriate team members. Develop contingency plans and risk response strategies to address these risks effectively.
Review the initial risk assessment: Revisiting the initial risk assessment conducted during the project planning phase. Identify the risks that have not been fully mitigated or eliminated.
Use checklists and templates: Utilize predefined risk checklists and templates specific to the project domain or industry. These resources can help ensure that common residual risks are not missed during the assessment process.
Analyze project changes: Assess the impact of any changes during project execution. Changes in scope, resources, technology, or stakeholders can introduce or modify new risks. Evaluate how these changes may affect the residual risks.
Communicate and engage: Share the findings of the residual risk assessment with the project team and stakeholders. Foster open communication and encourage feedback to ensure a comprehensive understanding of the identified risks.
To mitigate residual risks and secondary risks, project managers can employ the following strategies:
As discussed above, to mitigate risks, you must first identify them. Next comes prioritizing risks based on their potential impact and likelihood of occurrence so the project manager can focus their mitigation efforts on the most critical risks.
Let’s understand this with an example:
In a software development project, a project manager identifies risks such as system integration issues, scope creep, and cybersecurity vulnerabilities. Through risk assessment, the project manager evaluates each risk’s potential impact and likelihood of occurrence.
System integration issues are determined to have a high potential impact as they can disrupt the software’s functionality and delay the project.
Furthermore, the likelihood of occurrence is considered high due to complex dependencies among various systems. Consequently, the project manager prioritizes this risk as a high-priority risk and implements risk mitigation strategies like conducting thorough compatibility testing and establishing clear communication channels among development teams.
Scope creep, which refers to the uncontrolled expansion of project scope, is identified as having a moderate potential impact and the likelihood of occurrence. The project manager categorizes it as a medium-priority risk and implements change control processes, frequent stakeholder engagement, and regular scope reviews to effectively manage and mitigate scope creep.
By prioritizing risks based on their potential impact and likelihood of occurrence, project managers can focus their attention, resources, and mitigation efforts on the risks that pose the greatest threats to the project’s success.
These days, multiple software applications can aid in risk management by streamlining risk identification, assessment, and monitoring processes. These tools can automate data collection, analysis, and reporting, enabling more effective risk mitigation.
In addition to leveraging project management software and risk management tools, using artificial intelligence (AI) and machine learning (ML) can further enhance risk management processes.
Risk mitigation with AI technologies can facilitate advanced risk identification, analysis, and prediction capabilities like risk prediction and early warning systems, risk assessment automation, AI-mediated data analysis & more.
These technologies can identify hidden patterns and correlations in the data, enabling more accurate risk assessment and prioritization. NLP techniques can analyze unstructured data sources, such as project documentation, reports, and communication logs.
Machine Learning models can learn from historical risk data to improve risk assessment and provide insights into previously unknown risks.
As a project manager, your work doesn’t end at simply identifying the risks; it also involves developing a comprehensive risk response plan for each identified risk. This involves determining appropriate actions to avoid, transfer, mitigate, or accept the risk.
Here are some actionable insights to consider when developing a risk response plan:
A. Avoidance
Identify risks that can be completely avoided by changing project plans, approaches, or strategies.
Consider alternative solutions or methodologies that eliminate the possibility of the risk occurring.
Allocate resources to alternative activities or paths that minimize exposure to the project.
Example: In a software development project, if a specific technology poses a high-security risk, the project manager may decide to avoid the risk by switching to a more secure technology or architecture.
B. Transfer
Identify risks that can be transferred to a third party, such as an insurance company, subcontractor, or vendor.
Ensure appropriate contractual agreements are in place to transfer the responsibility and impact of the risk.
Evaluate the cost-effectiveness of transferring the risk versus managing it internally.
Example: In a construction project, the project manager may transfer the risk of delayed material delivery to the supplier by including penalty clauses in the contract, ensuring the supplier bears the financial consequences of any delays.
C. Mitigation
Identify risks that can be mitigated by implementing proactive measures to reduce their probability or impact.
Develop specific action plans, controls, or safeguards to minimize the likelihood or consequences of the risk.
Allocate resources, time, and budget to implement the mitigation measures effectively.
Example: In a marketing campaign project, the risk of low customer response rates can be mitigated by conducting thorough market research, targeting the right audience, and crafting compelling messaging to increase the chances of a positive response.
D. Acceptance
Identify risks that are deemed acceptable and within the organization’s risk tolerance.
Develop contingency plans or fallback options to address the impact if the risk materializes.
Continuously monitor the risk to detect changes in the risk landscape that may require a different response.
Example: In a product development project, the project manager may accept the risk of minor design flaws and plan to address them through post-launch updates or releases, understanding that they do not significantly impact the overall project goals.
It’s important to note that the risk response plan should be documented, communicated to stakeholders, and periodically reviewed and updated throughout the project lifecycle.
Contingency planning is a critical aspect of risk management that involves creating plans to address potential residual and secondary risks. These plans outline alternative approaches or actions to be taken if specific risks materialize. It may include steps like:
Building Alternative Scenarios
Project managers can develop alternative scenarios that account for the occurrence of identified risks. Consider various “what-if” situations and outline specific actions, tasks, or strategies for each scenario.
You can define triggers or indicators that signal the need to activate specific contingency plans.
Example 1: In supply chain management
Trigger: A supply failure or disruption in the supply chain that affects the availability of critical materials or components.
Indicator: A significant delay in the delivery of essential supplies, a sudden increase in product defects or quality issues, or the bankruptcy or financial instability of a critical supplier can be indicators to activate the triggers.
Example 1: Research and Development project
Trigger: Significant deviation from projected timelines, budget overruns, or technical obstacles that impede progress or compromise project goals.
Indicator: Failure to achieve critical milestones within the defined timeframe, significant changes in project scope or objectives, or the inability to overcome identified technical challenges.
Resource Allocation
Determine the necessary resources, such as personnel, budget, equipment, or materials, to implement contingency plans.
Ensure the availability and accessibility of these resources to respond to risks as they arise effectively. Consider the potential impact on the project schedule and budget when allocating resources for contingency plans.
Decision-Making Authority
Clearly define individuals’ decision-making authority and responsibilities in implementing contingency plans. Designate critical decision-makers who can assess the situation, activate the appropriate contingency plan, and communicate effectively with stakeholders.
Communication and Stakeholder Engagement
Establish a communication plan to inform stakeholders, team members, and relevant parties about the contingency plans and the circumstances that would trigger their implementation.
Ensure that all involved parties know their roles and responsibilities during contingency situations.
Also Read: Why is stakeholder management important?
Risk monitoring and control is a proactive process that involves:
Continuously monitoring identified risks throughout the project lifecycle.
Regularly assessing the effectiveness of implemented risk mitigation strategies.
Making necessary adjustments.
This approach allows project managers to address emerging risks promptly and assess residual risks.
For example, during a software development project’s risk monitoring and assessment process, the project manager identifies an emerging risk related to a recently discovered vulnerability in a software component being used. The project manager promptly takes the following actions:
Mobilize the software development team to analyze the impact and potential consequences of the vulnerability.
Collaborates with cybersecurity experts to understand the severity and possible countermeasures.
Adjusts the risk mitigation strategy by implementing additional security measures, such as patching the software component, conducting security testing, or seeking an alternative component.
Communicates the updated risk mitigation strategy to the relevant stakeholders and ensure its proper implementation.
Residual risks and secondary risks play significant roles in project management. By understanding their differences, project managers can proactively identify, assess, and mitigate these risks, ensuring project success. With this knowledge, project managers can confidently navigate the intricacies of risk management, minimizing the potential negative impacts and maximizing project outcomes.
Want to become a certified project manager? Select the best Edbrick course for you and strengthen your employability in the competitive job market.

September 25 2023
7 min read

September 5 2023
8 min read

July 18 2023
6 min read

June 12 2023
5 min read